Mobile payment technology and payments security is light-years ahead of just a few years ago. As scammers have found ways to take advantage of payment methods, mobile phones have stepped up to offer a more secure and convenient way to pay.
Unfortunately, scammers understand that they will have a difficult time defrauding both businesses and customers during a “Card Present” transaction. So, what do they focus on instead? “Card Not Present” transactions, such as payments made online or over the phone.
With this is mind, companies must now offer the best available technology while also maintaining top-of-the-line security. The question on everyone’s mind is, “How do you do that in a mobile phone and virtual environment?” The answer is PCI compliance.
The Industry Standard for Security

The industry standard is PCI DSS, Payment Card Industry Data Security Standard. PCI originally focused on in-person fraud opportunities, such as someone stealing a credit card number at a gas station or someone grabbing a new credit card out of a victim’s mailbox. And while these crimes still happen, consumers now have a more modern threat: virtual fraud.
Data security is a high priority everywhere. With Voice Over IP (VOIP) telephones used in many industries, the PCI standard consistently evolves to include relevant policies, such as:
- Not storing card information on the phone company’s servers
- Increasing the number of recorded conversations, thereby preventing fraudulent transactions or catching one in the act
- Securing the line for all phone payments, including IVR (Interactive Voice Response) lines
- Using DTMF masking technology (dual-tone multifrequency tones) to ensure that neither the VOIP company nor your cell phone provider has the card information saved on their servers.
If you want to see how well your organization is covering payments security, you can check out the PCI Security Standards Council’s Protecting Telephone-Based Payment Card Data presentation.
Keeping transactions safe is not only the responsibility of your business, however; customers should also make sure their mobile devices are secure.
Your Phone Is More Secure Now
Accessing the internet on your mobile device is both safe and secure, often even more so than on a desktop computer. This excellent piece on “20 Ways to Secure Your Phone” outlines the reasons why.
The threat to mobile transactions is not tied directly to the act of going online; it is from the secret malware that can be attached to a downloaded app. An easy workaround is to make sure your apps are up to date and delete any that are not in regular use. This will help you and your customers stay secure when phones are used to make payments.
So what does your company do to make sure its mobile app transactions are secure?
Two easy ways to secure a mobile app is to enable two-factor authentication and code or biometric-based logins. Two-factor authentication verifies their identity via two separate means. The first step is when the user inputs their username and password into your mobile app. This triggers the second step: a separate mobile app, such as Google Authenticator, sends the user a one-time code that they are expected to input into your company app. It’s as easy as copying the code from one app and then pasting it into the other.
Here is an example of a 3rd party authentication app.
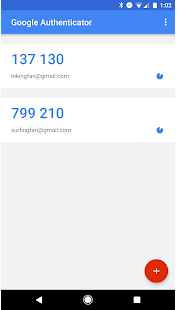
Authentication codes expire after two minutes, thereby adding an extra layer of security. Code, fingerprint, and facial recognition logins are more common for everyday mobile device users than two-factor authentication, but all are effective. Make sure you implement one of these security measures and recommend heightened verification protocols to your customers.
Conclusion
When companies talk about mobile payment security, they need to focus on process and technology. By securing your network, using two-factor authentication, and keeping customer data off all relevant networks, your business can provide updated security to your customers.
No one can make a network 100% secure, but maintaining PCI compliant security measures can help your company mitigate risk and accept payments safely and securely.
